Nested Home Lab – Part 5 – Adding an Active Directory identity source to your PSC / VCSA

As in the previous post, if you haven’t done so already, you need to install the Client integration plugin which can be found in the iso at vcsaVMware-ClientIntegrationPlugin-6.0.0.exe.
Firstly unpack the ISO to your local drive. C:/temp for example.
1. Double click on vcsa-setup.html. (found in the unpacked ISO).
3. Select Install
5. Enter in the IP address, username (usually root) and the password of the ESXi server you are deploying the PSC to.Click Next.
6. Accept the certificate warning by clicking Yes.
7. Enter in the name of the VCSA and give it a password. Click Next.
8. On this screen you have three choices. For our lab we’ll select “Install vCenter Server (Requires external Platform Services Controller)“. Click Next.
9. Now here we’ll want to enter in the details of the PSC we deployed previously, entering in the PSC name and the SSO password. Its usually best to leave the SSO port at 443. Click Next.
10. Leave the appliance size at tiny. Click Next.
11. Select the datastore you want to deploy into and select “Enable Thin Disk Mode“. Click Next.
12. Select “Use an embedded database (vPostgres). Click Next.
13. Carefully, enter in the networking details, tick “Enable ssh”. Click Next.
14. Check all your config details. Click Finish
So back again.
In this post we’ll look at installing the Platform Services Controller (PSC).
Forgetting about ESX for a minute, this new iteration of vSphere is, in my opinion, a huge leap forward for administrators. It feels like the virtual appliance architecture has finally come of age. The split of duties makes a great deal of sense. The PSC is responsible for Single Sign On (SSO), Licensing, and as a Certificate Authority, while the VCSA hosts the inventory service, the web client and others.
So why on different appliances for this lab? Well going forward, in future blog posts, we’ll look at connecting a second VCSA to the PSC.
This first VCSA and PSC will lay the foundation for this and future labs
OK onward.
To install the VCSA and/or PSC you you will need to install the VMware client intergration plugin. can be found in the iso at
This part of the installer does assume that you have a DC up and running. If you don’t you should get one setup before continuing as we will need it later, if you choose to follow that part of the guide.
Once that’s done we can fire up the installer and get the PSC installed.
Firstly unpack the ISO to your local drive. C:/temp for example.
1. Double click on vcsa-setup.html. (found in the unpacked ISO).
11. Networking is King here and you’ll need to be vigilant going through this. For the time sync select “Synchronize appliance with ESXi host” and tick “Enable ssh”. Click Next.
| Use | Example IP Range | Note |
| VM and Management | 192.168.0.0 | Best to use you existing home network. |
| VSAN (vlan 30) | 192.168.100.0 | Internal Only |
| vMotion (vlan 40) | 192.168.110.0 | Internal Only |
It is considered best practice to separate out various types of network traffic. Usually you would separate out your VM traffic from your management but for this lab we will keep them together. We will separate out vMotion and VSAN traffic though.
ESXi: When I’m designing a vSphere environment with rack mount servers in mind I usually separate management traffic out into a separate standard virtual switch (2 x 1g ports) and all other traffic is sent to 2 x 10g ports through a distributed virtual switch using vlans to separate the traffic further and NIOC to control bandwidth.
All righty then, what’s this going to look like for us?
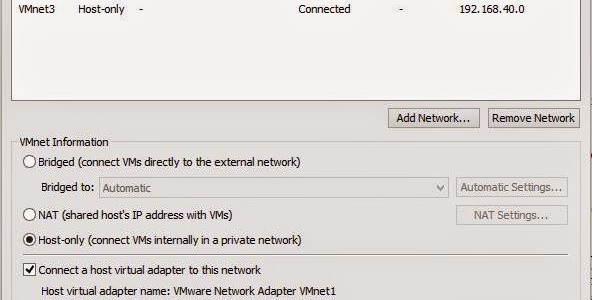
In Workstation:
So far, so good. For Workstation nothing else needs to be done.
As you can see from the ESXi image above I haven’t specified a physical adapter for vSwitch1, With ESXi if network traffic is on the same VLAN and on the same virtual switch, it won’t go the the physical switch. The virtual switch, an in memory construct, will just pass the traffic along, however if you need to cross VLANs, the traffic will need to be passed to the physical switch for routing across VLANs. In this case, its very handy as we won’t want traffic to pass between the VSAN port group and the vMotion port group. EDIT: What we want to do is set-up the LAN port group with VLAN 4095. This will enable ESXi to pass the vlan traffic about correctly.
Now is ESXi we need to make two changes to the vMotion and VSAN port groups, Enable Promiscuous Mode and Forget Transmits:
William Lam of Virtually Ghetto has a great write up here discussing the reasons for this.
So those are the networking eccentricities, Next we’ll look at getting our first VCSA with a dedicated Platform Services Controller up and running.
Just a note: I had hoped to post this sooner but family and holiday commitments took over.