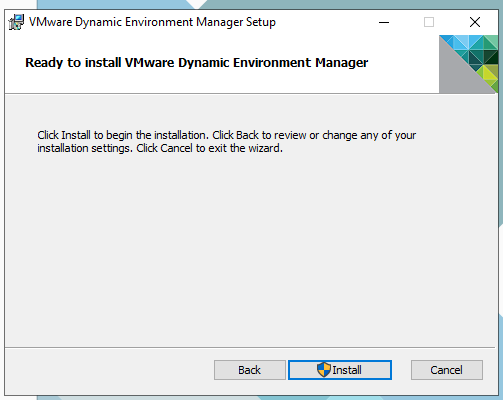
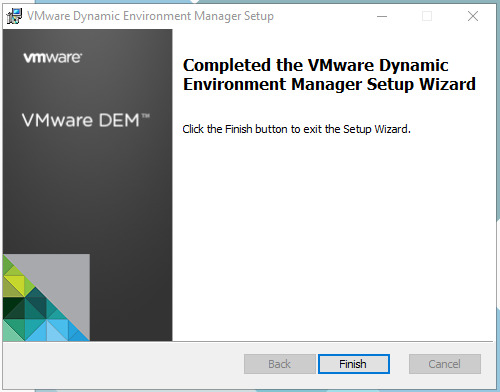
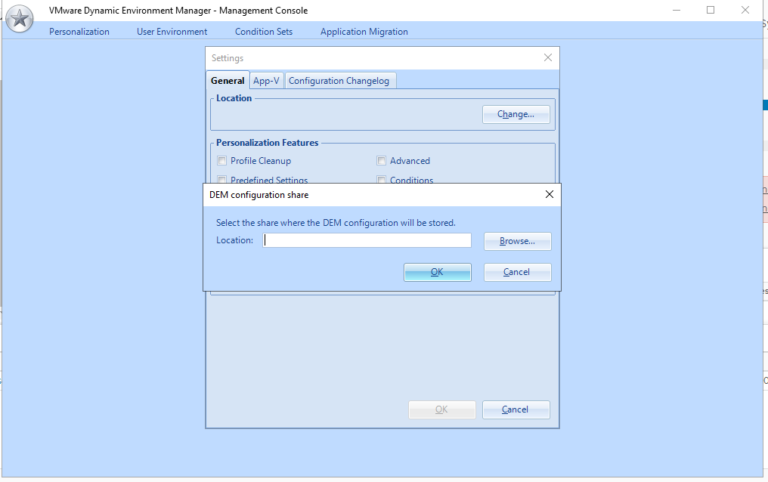
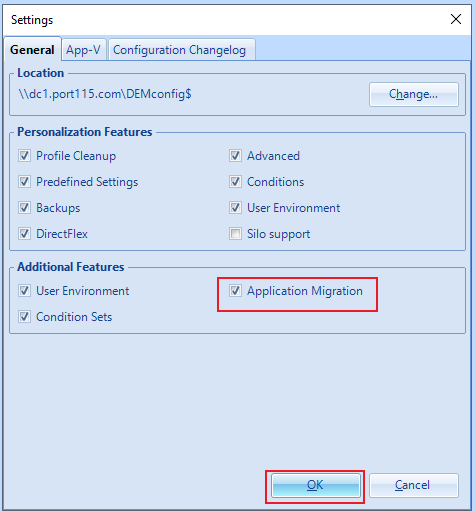
This is an event I look forward to all year and once again it didn’t disappoint.
 This was the second year at the National Space Centre in Leicester, which saw me getting up at 5:30 am to take a couple of trains, and one bus to arrive there on time. Totally worth the journey. This year the UK VMUG was a couple of weeks earlier than last year.
This was the second year at the National Space Centre in Leicester, which saw me getting up at 5:30 am to take a couple of trains, and one bus to arrive there on time. Totally worth the journey. This year the UK VMUG was a couple of weeks earlier than last year.
This venue is about the right size for this event and the whole space theme lends a bit of novelty to the proceedings. I’m still surprised after all these years that this event is free.
As is becoming tradition Joe Baguley gave the opening keynote. He went into a fair bit of detail about AI and the various misconceptions between (what is commonly thought of as AI), machine learning, deep learning, and data analytics which was very interesting. The closing keynote was given by Dr Anu Ojha, but more about that later.
There was a great collection of vendors there. Lots of very interesting tech on show, including some old favourites like Veeam, Zenoss, HP, and Google Cloud. (to name a few).
My Favourite Sessions, in no particular order.
There is always a good selection of sessions and the first one I attended was given by Ed Gummett of Veeam. I’m a big fan of Veeam Backup and Replication and was looking forward to finding out whats new. The discussion revolved around cloud and how Veeam has grown its products to take advantage of that. Of particular interest was the new features coming in version 10.
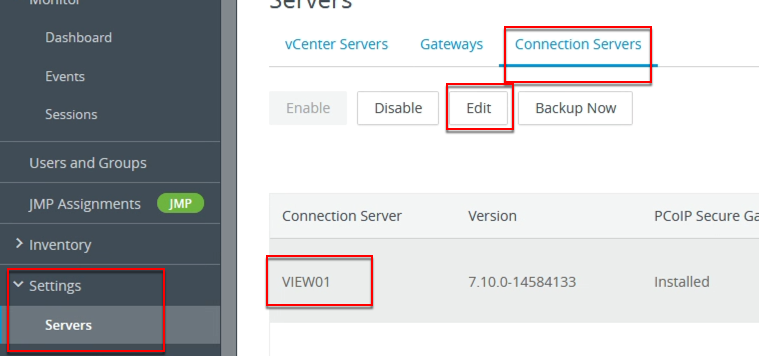
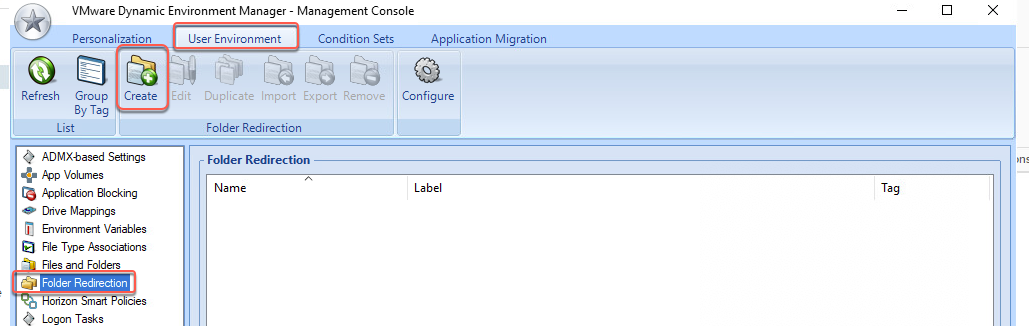
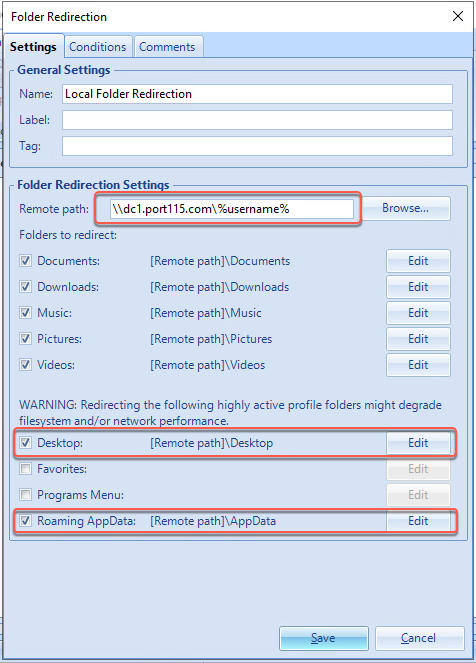
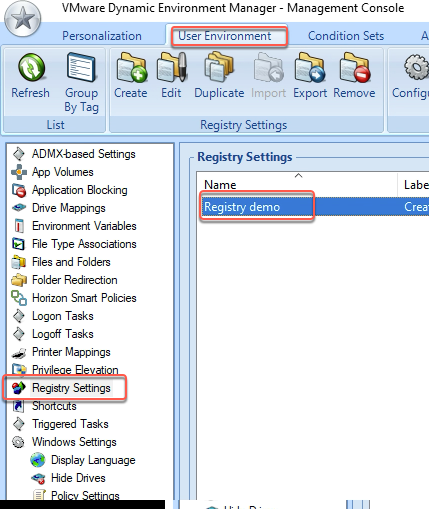
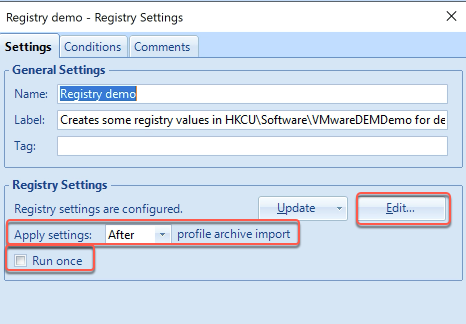
From there I went across to “VMware: What’s new in VMware End User Computing” presented by Darren Hirons. Much of the talk was about the new features in Workspace One, Horizon Cloud, and a bit about App Volumes 4. If you are into EUC take a look over at VMware’s EUC Blog here. After the lecture I went up to present Darren with a bunch of questions i had about the upcoming App Volumes 4.0.

After lunch and walk around the centre, I attended “VMware: NSX-T Container Level Networking & Security” by Joshua Coulling. This talk actually surprised me quite a bit. I though it would be quite dry but in actual fact I found it interesting how NSX and containers can work together as well as gaining a better understanding of kubernetes as a whole. Joshua clearly know his stuff and was happy to answer my “no-so-bright” questions when I went up to meet him after the talk.
Closing Keynote.
This was so unexpected and absolutely fascinating. The closing keynote was given by Professor Anu Ojha. He took us through current space exploration, the benefits of investing in space technology and research (which provides quite a good financial return) and its practical applications. There is a push to invest more, including returning to the moon in 2024 and further out, a manned mission to mars. the talk was about 45 minutes long and I just sat there in completely mesmerised at how incredible “space science” really is.

And that wrapped up another really great UK VMUG.
As always I came away with a bunch of new information, both from vendors and VMware itself. It can be nicer to be in these smaller venues as I find it easier to approach the speakers after the talks and take up a bit of their time with questions.
If you haven’t been before, what are you waiting for?
 vExpert 2020! What a great way to wake up.
vExpert 2020! What a great way to wake up.